November 13, 2018Swati Khandelwal

It’s Patch Tuesday once again…time for another round of security updates
for the Windows operating system and other Microsoft products.
This month Windows users and system administrators need to immediately
take care of a total of 63 security vulnerabilities, of which 12 are
rated critical, 49 important and one moderate and one low in severity.
Two of the vulnerabilities patched by the tech giant this month are listed as publicly known at the time of release, and one flaw is reported as being actively exploited in the wild by multiple cybercriminal groups.
ATTENTION: Click Here To Get Over $100,000 Money Transfer Through Bank Transfer Hackers!!!
ATTENTION: Get Your Hacked Western Union MTCN Transfer and Cash Out Over $2500 within minutes!!!
ATTENTION: Click Here For Your Blank/Cloned ATM Cards for ATM Cashout and Online Purchase!!!
Zero-Day Vulnerability Being Exploited by Cyber Criminals
The zero-day vulnerability, tracked as CVE-2018-8589,
which is being exploited in the wild by multiple advanced persistent
threat groups was first spotted and reported by security researchers
from Kaspersky Labs.
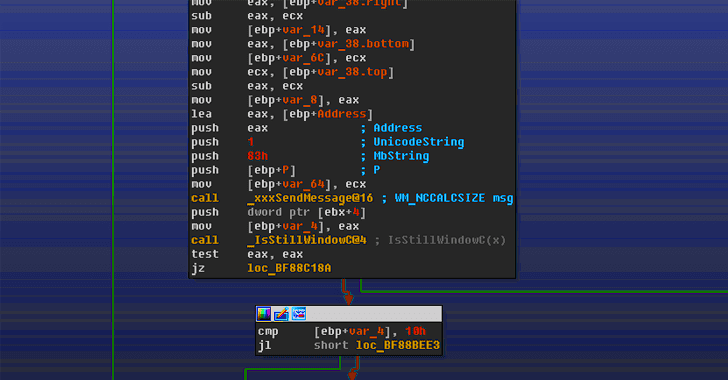
The flaw resides in the Win32k component (win32k.sys), which if
exploited successfully, could allow a malicious program to execute
arbitrary code in kernel mode and elevate its privileges on an affected
Windows 7, Server 2008 or Server 2008 R2 to take control of it.
“The exploit was executed by the first stage of a malware installer in order to gain the necessary privileges for persistence on the victim’s system. So far, we have detected a very limited number of attacks using this vulnerability,” Kaspersky said.
Two Publicly Disclosed Zero-Day Vulnerabilities
The other two publicly known zero-day vulnerabilities which were not
listed as under active attack reside in Windows Advanced Local Procedure
Call (ALPC) service and Microsoft’s BitLocker Security Feature.
The flaw related to ALPC, tracked as CVE-2018-8584,
is a privilege escalation vulnerability that could be exploited by
running a specially crafted application to execute arbitrary code in the
security context of the local system and take control over an affected
system.
Advanced local procedure call (ALPC) facilitates high-speed and secure
data transfer between one or more processes in the user mode.
The second publicly disclosed vulnerability, tracked as CVE-2018-8566,
exists when Windows improperly suspends BitLocker Device Encryption,
which could allow an attacker with physical access to a powered-off
system to bypass security and gain access to encrypted data.
BitLocker was in headlines earlier this month for a separate issue that could expose Windows users encrypted data due to its default encryption preference and bad encryption on self-encrypting SSDs.
Microsoft did not fully address this issue; instead, the company simply
provided a guide on how to manually change BitLocker default encryption
choice.
November 2018 Patch Tuesday: Critical and Important Flaws
Out of 12 critical, eight are memory corruption vulnerabilities in the
Chakra scripting engine that resides due to the way the scripting engine
handles objects in memory in the Microsoft Edge internet browser.
All the 8 vulnerabilities could be exploited to corrupt memory, allowing
an attacker to execute code in the context of the current user. To
exploit these bugs, all an attacker needs to do is tricking victims into
opening a specially crafted website on Microsoft Edge.
Rest three vulnerabilities are remote code execution bugs in the Windows
Deployment Services TFTP server, Microsoft Graphics Components, and the
VBScript engine. All these flaws reside due to the way the affected
software handles objects in memory.
The last critical vulnerability is also a remote code execution flaw
that lies in Microsoft Dynamics 365 (on-premises) version 8. The flaw
exists when the server fails to properly sanitize web requests to an
affected Dynamics server.
If exploited successfully, the vulnerability could allow an
authenticated attacker to run arbitrary code in the context of the SQL
service account by sending a specially crafted request to a vulnerable
Dynamics server.
| Windows Deployment Services TFTP Server Remote Code Execution Vulnerability | CVE-2018-8476 | Critical |
| Microsoft Graphics Components Remote Code Execution Vulnerability | CVE-2018-8553 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8588 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8541 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8542 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8543 | Critical |
| Windows VBScript Engine Remote Code Execution Vulnerability | CVE-2018-8544 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8555 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8556 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8557 | Critical |
| Chakra Scripting Engine Memory Corruption Vulnerability | CVE-2018-8551 | Critical |
| Microsoft Dynamics 365 (on-premises) version 8 Remote Code Execution Vulnerability | CVE-2018-8609 | Critical |
| Azure App Service Cross-site Scripting Vulnerability | CVE-2018-8600 | Important |
| Windows Win32k Elevation of Privilege Vulnerability | CVE-2018-8589 | Important |
| BitLocker Security Feature Bypass Vulnerability | CVE-2018-8566 | Important |
| Windows ALPC Elevation of Privilege Vulnerability | CVE-2018-8584 | Important |
| Team Foundation Server Cross-site Scripting Vulnerability | CVE-2018-8602 | Important |
| Microsoft Dynamics 365 (on-premises) version 8 Cross Site Scripting Vulnerability | CVE-2018-8605 | Important |
| Microsoft Dynamics 365 (on-premises) version 8 Cross Site Scripting Vulnerability | CVE-2018-8606 | Important |
| Microsoft Dynamics 365 (on-premises) version 8 Cross Site Scripting Vulnerability | CVE-2018-8607 | Important |
| Microsoft Dynamics 365 (on-premises) version 8 Cross Site Scripting Vulnerability | CVE-2018-8608 | Important |
| Microsoft RemoteFX Virtual GPU miniport driver Elevation of Privilege Vulnerability | CVE-2018-8471 | Important |
| DirectX Elevation of Privilege Vulnerability | CVE-2018-8485 | Important |
| DirectX Elevation of Privilege Vulnerability | CVE-2018-8554 | Important |
| DirectX Elevation of Privilege Vulnerability | CVE-2018-8561 | Important |
| Win32k Elevation of Privilege Vulnerability | CVE-2018-8562 | Important |
| Microsoft SharePoint Elevation of Privilege Vulnerability | CVE-2018-8572 | Important |
| Microsoft Exchange Server Elevation of Privilege Vulnerability | CVE-2018-8581 | Important |
| Windows COM Elevation of Privilege Vulnerability | CVE-2018-8550 | Important |
| Windows VBScript Engine Remote Code Execution Vulnerability | CVE-2018-8552 | Important |
| Microsoft SharePoint Elevation of Privilege Vulnerability | CVE-2018-8568 | Important |
| Windows Elevation Of Privilege Vulnerability | CVE-2018-8592 | Important |
| Microsoft Edge Elevation of Privilege Vulnerability | CVE-2018-8567 | Important |
| DirectX Information Disclosure Vulnerability | CVE-2018-8563 | Important |
| MSRPC Information Disclosure Vulnerability | CVE-2018-8407 | Important |
| Windows Audio Service Information Disclosure Vulnerability | CVE-2018-8454 | Important |
| Win32k Information Disclosure Vulnerability | CVE-2018-8565 | Important |
| Microsoft Outlook Information Disclosure Vulnerability | CVE-2018-8558 | Important |
| Windows Kernel Information Disclosure Vulnerability | CVE-2018-8408 | Important |
| Microsoft Edge Information Disclosure Vulnerability | CVE-2018-8545 | Important |
| Microsoft SharePoint Information Disclosure Vulnerability | CVE-2018-8578 | Important |
| Microsoft Outlook Information Disclosure Vulnerability | CVE-2018-8579 | Important |
| PowerShell Remote Code Execution Vulnerability | CVE-2018-8256 | Important |
| Microsoft Outlook Remote Code Execution Vulnerability | CVE-2018-8522 | Important |
| Microsoft Outlook Remote Code Execution Vulnerability | CVE-2018-8576 | Important |
| Microsoft Outlook Remote Code Execution Vulnerability | CVE-2018-8524 | Important |
| Microsoft Word Remote Code Execution Vulnerability | CVE-2018-8539 | Important |
| Microsoft Word Remote Code Execution Vulnerability | CVE-2018-8573 | Important |
| Microsoft Excel Remote Code Execution Vulnerability | CVE-2018-8574 | Important |
| Microsoft Project Remote Code Execution Vulnerability | CVE-2018-8575 | Important |
| Microsoft Outlook Remote Code Execution Vulnerability | CVE-2018-8582 | Important |
| Windows Search Remote Code Execution Vulnerability | CVE-2018-8450 | Important |
| Microsoft Excel Remote Code Execution Vulnerability | CVE-2018-8577 | Important |
| Internet Explorer Memory Corruption Vulnerability | CVE-2018-8570 | Important |
| Microsoft JScript Security Feature Bypass Vulnerability | CVE-2018-8417 | Important |
| Windows Security Feature Bypass Vulnerability | CVE-2018-8549 | Important |
| Microsoft Edge Spoofing Vulnerability | CVE-2018-8564 | Important |
| Active Directory Federation Services XSS Vulnerability | CVE-2018-8547 | Important |
| Team Foundation Server Remote Code Execution Vulnerability | CVE-2018-8529 | Important |
| Yammer Desktop Application Remote Code Execution Vulnerability | CVE-2018-8569 | Important |
| Microsoft Powershell Tampering Vulnerability | CVE-2018-8415 | Important |
| .NET Core Tampering Vulnerability | CVE-2018-8416 | Moderate |
| Microsoft Skype for Business Denial of Service Vulnerability | CVE-2018-8546 | Low |
This month’s security update also covers 46 important vulnerabilities in
Windows, PowerShell, MS Excel, Outlook, SharePoint, VBScript Engine,
Edge, Windows Search service, Internet Explorer, Azure App Service, Team
Foundation Server, and Microsoft Dynamics 365.
Users and system administrators are strongly advised to apply the above
security patches as soon as possible in order to keep hackers and cyber
criminals away from taking control of their systems.
For installing security patch updates, head on to Settings → Update
& security → Windows Update → Check for updates, or you can install
the updates manually.